Hack the Vote! Digital Election Rigging 2024
Decades of warnings and nothing has changed. Voting machines are not secure!
At DEF CON 2024, a significant event unfolded as reported by @TheDgtalEmpress on X, where a voting machine was compromised, highlighting ongoing security vulnerabilities in election equipment. This incident at the Voting Village, an event at DEF CON where hackers test the security of voting systems, underscores the persistent and unresolved security issues with voting machines that have been noted since at least 2018. Despite annual discoveries of such vulnerabilities, the timing and complexity of implementing fixes mean that many identified security gaps remain unaddressed by the time elections occur.
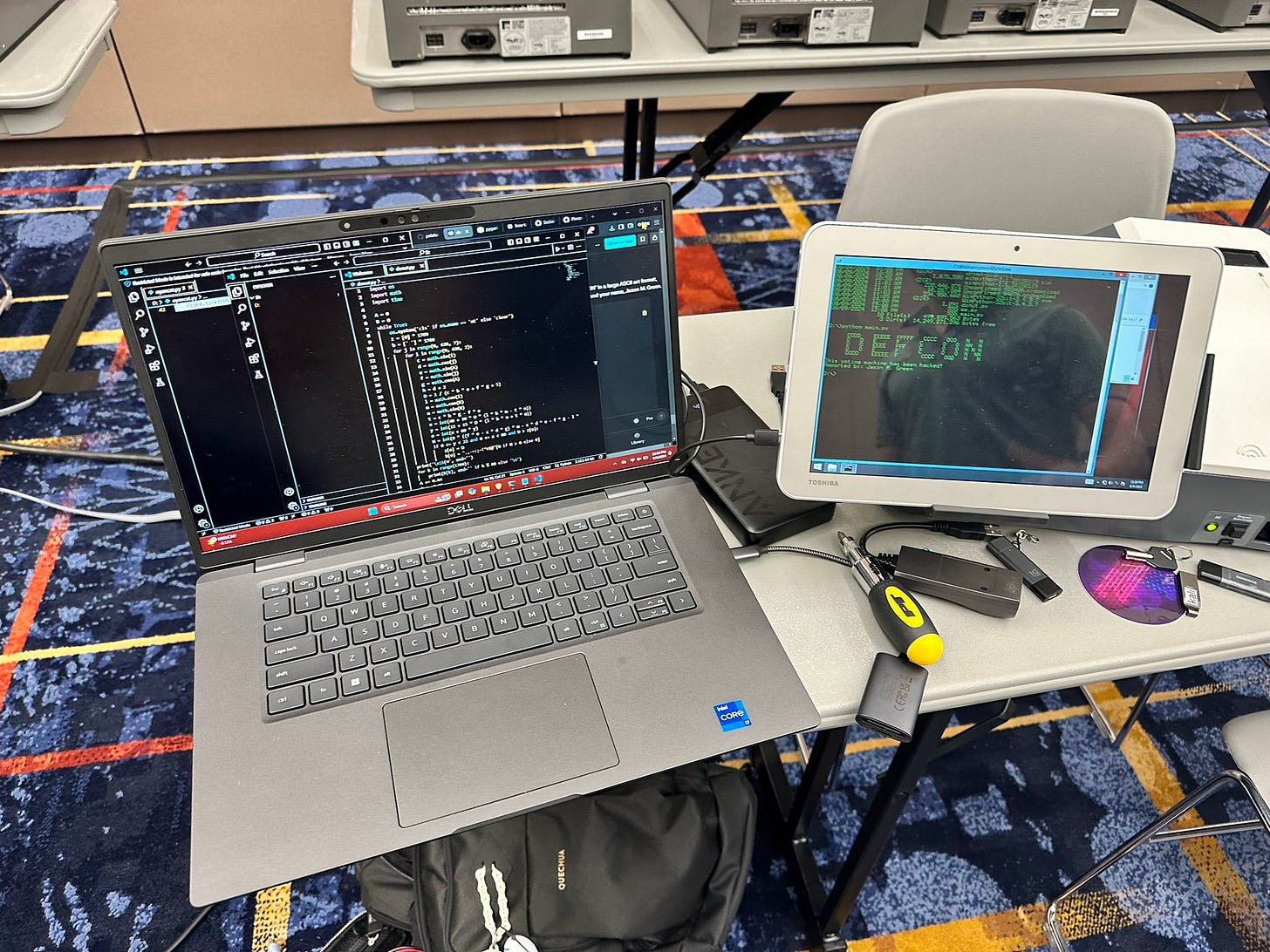
This ongoing problem not only raises concerns about potential election interference but also feeds into broader skepticism about election integrity, especially in the context of recent political narratives around electoral fraud. Efforts like the SECURE IT Act, introduced in both the Senate and House, aim to enhance voting machine security through mandated penetration testing and a pilot program for cybersecurity researchers to disclose vulnerabilities, but as of the latest updates, these legislative measures are still in process.
Voting Machines Are Still Absurdly Vulnerable to Attacks - 2018
While Russian interference operations in the 2016 US presidential elections focused on misinformation and targeted hacking, officials have scrambled ever since to shore up the nation's vulnerable election infrastructure. New research, though, shows they haven't done nearly enough, particularly when it comes to voting machines.
The report details vulnerabilities in seven models of voting machines and vote counters, found during the DefCon security conference's Voting Village event. All of the models are in active use around the US, and the vulnerabilities—from weak password protections to elaborate avenues for remote access—number in the dozens. The findings also connect to larger efforts to safeguard US elections, including initiatives to expand oversight of voting machine vendors and efforts to fund state and local election security upgrades.
"We didn't discover a lot of new vulnerabilities," says Matt Blaze, a computer science professor at the University of Pennsylvania and one of the organizers of the Voting Village, who has been analyzing voting machine security for more than 10 years. "What we discovered was vulnerabilities that we know about are easy to find, easy to reengineer, and have not been fixed over the course of more than a decade of knowing about them. And to me that is both the unsurprising and terribly disturbing lesson that came out of the Voting Village."
https://www.wired.com/story/voting-machine-vulnerabilities-defcon-voting-village/
https://www.votingvillage.org/
Here's a summary of the vulnerabilities in voting machines highlighted in the DEF CON 26 Voting Village Report 2018:
General Security Concerns: The report underscores that many voting machines in use are outdated, running software from the 1990s or early 2000s, which inherently lack modern security features. This age gap in technology leaves them vulnerable to both physical and digital attacks.
Physical Access Vulnerabilities: Many vulnerabilities require physical access to the machines. However, once accessed, attackers could manipulate the hardware or software, including installing unauthorized software or altering votes.
Weak Password Protections: Several machines had easily guessable or default passwords, which could allow unauthorized access to change settings or manipulate vote counts.
Remote Access Vulnerabilities: Some machines were found to have vulnerabilities that could potentially allow remote access, either through direct internet connections or by exploiting other network vulnerabilities.
Lack of Auditability: Many systems did not provide a reliable paper trail or lacked mechanisms for post-election audits, making it difficult to verify the electronic results.
Software Vulnerabilities: Outdated software often contains known vulnerabilities that have not been patched. This includes issues like buffer overflows, insecure configurations, and lack of encryption for data in transit or at rest.
Network Security: Some voting equipment was found to be connected to the internet or local networks without proper security measures, potentially allowing for attacks through these connections.
E-poll Books: These devices, used for checking in voters, also exhibited vulnerabilities, including hidden Ethernet ports that could be used for unauthorized access if connected.
Persistence of Known Issues: Many of the vulnerabilities identified were not new; they had been known for over a decade but remained unaddressed in many systems still in use.
Model Specific Issues: The report detailed specific vulnerabilities in various models, like the ES&S Model 650, which, despite being discontinued, still showed significant security flaws when tested.
The overarching theme from the report is the critical need for updating election infrastructure, not just in terms of technology but also in practices like ensuring a verifiable paper trail, regular security audits, and immediate patching of known vulnerabilities. The report's findings emphasize the importance of moving towards more secure voting systems that incorporate these security measures as standard practice.
#HackTheVote & Election Rigging YouTube Playlist
The nation’s best hackers found vulnerabilities in voting machines — but no time to fix them - 2024
LAS VEGAS — Some of the best hackers in the world gathered in Las Vegas over the weekend to try to break into voting machines that will be used in this year’s election — all with an eye to helping officials identify and fix vulnerabilities.
The problem? Their findings will likely come too late to make any fixes before Nov. 5.
In one sense, it’s the normal course of events: Every August, hackers at the DEF CON conference find security gaps in voting equipment, and every year the long and complex process of fixing them means nothing is implemented until the next electoral cycle.
But Election Day security is under particular scrutiny in 2024. That’s both because of increasing worries that foreign adversaries will figure out how to breach machines, and because President Donald Trump’s unsubstantiated allegations of widespread fraud in 2020 undermined confidence in the vote among his supporters.
As a result, many in the election security community are bemoaning the fact that no system has been developed to roll out fixes faster and worrying that the security gaps that get identified this year will provide fodder for those who may want to question the results.
“As far as time goes, it is hard to make any real, major, systemic changes, but especially 90 days out from the election,” said Catherine Terranova, one of the organizers of the DEF CON “Voting Village” hacking event. She argued that’s particularly troubling during “an election year like this.”
https://politico.com/news/2024/08/12/hackers-vulnerabilities-voting-machines-elections-00173668
Former officials warn campaigns to ‘buckle up’ — more hacks are likely
Experts and cyber professionals also worry that recent hack of Trump presidential campaign has echoes of the Russian attacks on Hillary Clinton’s 2016 presidential campaign.
https://www.politico.com/news/2024/08/11/presidential-campaign-cyber-attacks-00173516
Can online voting be secure? Experts try to hack new platform
LAS VEGAS: Hackers from around the world gathered in a small conference room in Las Vegas on Friday to test their skills against a new online voting platform, in a bid to learn what digital vulnerabilities exist in the next generation of election systems.
The platform, known as Secure Internet Voting, or SIV, is run by a US firm of the same name. Allowing people to vote from their phones or computers is already being used in small pilot programmes around the United States.
But it faces significant hurdles to greater deployment: most states do not allow for the widespread use of online voting due to security concerns, instead opting for paper ballots that are auditable.
“There are a lot of people that have determined that it’s only possible to create insecure internet voting,” SIV founder David Ernst said at the conference.
“We believe that there are modern tools and technologies that allow you to make it hyper-secure, with a higher level of security than you can currently achieve with paper.” SIV has already been used at a party level to select a candidate in a primary race, Ernst said.
Republican Celeste Maloy was selected as a congressional candidate in a vote powered by SIV in 2023. Maloy went on to win that seat in Utah’s 2nd congressional district in November last year.
$10,000 prize for successful hacker(s)
Voting security is on Americans’ minds, with some fearing this November’s presidential and congressional elections could be the target of foreign cyberattacks.
Senior national security officials say Russia and Iran are already targeting voters with online influence campaigns. During the 2016 and 2020 election cycles, Russian hackers targeted election offices and probed several voting machine companies.
The team behind SIV has offered $10,000 in prize money to be shared among any hackers who can successfully identify flaws in their system.
The event is taking place at the Def Con Hacking Conference, which brings thousands of cybersecurity professionals to Nevada for one weekend a year, and has been organised by Def Con’s election security group “Voting Village”. Voting Village founder Harri Hursti said the technology had promise, but that the possibility of widespread online voting could take decades to realise.
“There are a couple of mathematical approaches which might, in the future, make internet voting possible,” Hursti said. “The inventor of one of those technologies said he might solve it, but not in our lifetimes.”
https://www.dawn.com/news/1851551/can-online-voting-be-secure-experts-try-to-hack-new-platform
A Senate Bill Would Radically Improve Voting Machine Security
This year’s Intelligence Authorization Act would mandate penetration testing for federally certified voting machines and allow independent researchers to work on exposing vulnerabilities.
https://www.wired.com/story/a-senate-bill-would-radically-improve-voting-machine-security/
S.1500 - SECURE IT Act
Sponsor: Sen. Warner, Mark R. [D-VA] (Introduced 05/09/2023)
Committees: Senate - Rules and Administration
Latest Action: Senate - 05/09/2023 Read twice and referred to the Committee on Rules and Administration
A bill to amend the Help America Vote Act of 2002 to require the Election Assistance Commission to provide for the conduct of penetration testing as part of the testing and certification of voting systems and to provide for the establishment of an Independent Security Testing and Coordinated Vulnerability Disclosure Pilot Program for Election Systems.
Introduced in Senate (05/09/2023)
Strengthening Election Cybersecurity to Uphold Respect for Elections through Independent Testing Act or the SECURE IT Act
This bill requires certain actions to strengthen the security of U.S. voting systems.
Specifically, the bill requires the Election Assistance Commission (EAC) to conduct penetration testing (an evaluation method that enables researchers to search for vulnerabilities in a system) as part of the testing, certification, decertification, and recertification of voting system hardware and software by accredited laboratories.
Further, the National Institute of Standards and Technology must recommend entities to the EAC to carry out this penetration testing and the EAC must vote on the accreditation of any recommended entity.
The bill also directs the EAC to create a five-year pilot program for participating cybersecurity researchers to test for and disclose cybersecurity vulnerabilities in election systems.
https://congress.gov/bill/118th-congress/senate-bill/1500/all-info
H.R.7447 - SECURE IT Act
Sponsor: Rep. Spanberger, Abigail Davis [D-VA-7] (Introduced 02/23/2024)
Committees: House - House Administration; Science, Space, and Technology
Latest Action: House - 02/23/2024 Referred to the Committee on House Administration, and in addition to the Committee on Science, Space, and Technology, for a period to be subsequently determined by the Speaker, in each case for consideration of such provisions as fall within the jurisdiction of the committee concerned
Full Bill Text: https://www.congress.gov/bill/118th-congress/house-bill/7447/text
Summary
Electronic voting machines have been vulnerable to cyber attacks and election manipulation and fraud for over a decade. Introducing legislation to finally require proper penetration testing DURING AN ELECTION YEAR is a slap in the face and a ruse to question the outcome of the 2024 election.
The SECURE IT Act, while necessary, is highly questionable for two reasons:
This bill was introduced by Democrats in the House and Senate earlier this year and referred to committee (no action) while all indicators are that Republican Donald Trump is the likely winner come November 2024.
Over the past decade, hackers have warned about the vulnerabilities in all Electronic Voting Machines. Despite these warnings, anyone who questioned the outcome of the 2020 election was censored or outright banned from social media. Remember the slogan: “the most secure, fair election ever.”
I am not buying any of this bullshit any longer and that is what prompted me writing this article. Based on the narrative networks and perception management from legacy media outlets, here is the near future.
MY PREDICTION
Donald J. Trump will win the election on November 5th and become the 47th President of the United States of America.
Democrats will scream RUSSIA, RUSSIA, RUSSIA, and blame vulnerable voting machines, hacking, and foreign interference in the election: JUST LIKE THEY DID IN 2016.
Be ready, stay salty, and keep you eyes and ears open.







EPIC megathread on Election Rigging, electronic voting machine vulnerabilities, and more on X:
https://x.com/KanekoaTheGreat/status/1648462770936115202
Just keep doom-scrolling. It's worth the time.
Nothing digital is secure! ZERO !